





Our unique solution to make cyber security a breeze
- Manage all aspects of cyber security in one place
- Fully customisable solution with white label features
- View and manage organisation reports & track employee progress
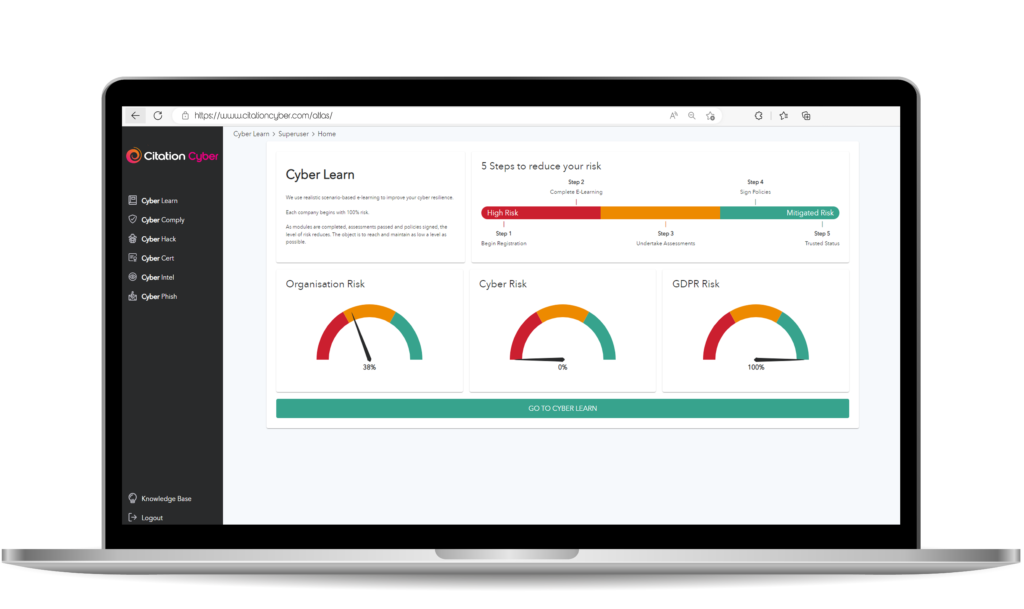
What we can do for your business
Our services are designed with your business in mind. Effectively protect
your devices, data, people and the infrastructure system which supports it all
Cyber Learn

Cyber Awareness Training
Scenario-based, interactive awareness training for all your staff covering four key areas of concern. Effectively reduce your cyber risk in real time.
Cyber Phish

Phishing Simulator
Schedule and manage phishing campaigns throughout your organisation. Keep your employees vigilant with targeted training.
Cyber Cert

Cyber Essentials Certification
Certify your organisation with Cyber Essentials and Cyber Essentials Plus. Simplified certification process with guided questionnaire and support.
Cyber Hack

Simulated Hacking
Penetration testing or simulated hacking of your website, network infrastructures, mobile apps, IoT devices and even physical security.
Cyber Intel

Intelligent Scanning
Reduce the risk of a cyber breach through our intelligence-led, cloud-based vulnerability scanning and third-party breach notifications.
Cyber Consult

Professional Consultancy
Designed for those who have compliance mandates such as PCI, GDPR, ISO. Our team of consultants have years of industry experience to support your business through the process.
Cyber Comply

Policy Compliance
Policy and document management to make meeting compliance a breeze. With 12 NCSC-certified policy templates to get you started.
Cyber sure

Cyber Liability Insurance
Our insurance and cyber risk management programs are tailored to your industry and organisation, based on risk insights.
Trusted cyber security advisors to companies worldwide
0
%
of breaches are the result of internal threats.
0
/10
of companies suffer at least one cyber attack per year.
£
0
m
the average cost of breach in 2020.















Verified
With social distancing this years audit was a very different affair but Mitigate Cyber handled it well, assigned last years auditor and made the process as painless as possible.
The pre-audit questionnaire platform changes are also a welcome improvement.
The company have been working on more than a name change and it shows in improvements across the audit process.
Remote User
12/03/2021
Verified
We have used Mitigate Cyber for years, they have always been helpful with all our audits we've had with them across multiple businesses. We will be using them in the future without any hesitation.
Matt
11/03/2021
Verified
smooth process, fast response, and knowledgeable auditors
scott mcconnell
11/03/2021
Verified
We recently renewed our Cyber Essentials basic certificate with Mitigate Cyber and then successfully achieved the Plus certification for the first time.
The entire process was communicated extremely well by both auditors and I would highly recommend them to anyone looking to gain this certification for their organisation.
Tony Lofts
10/03/2021
Verified
Mitigate have always been flexible, professional and great value for money - would highly recommend if you are looking to get Cyber Essentials certification!
Peter Hanslip
10/03/2021
Verified
Have used MitigateCyber for a couple of years for Cyber Essentials. I found them very helpful and was a simple process.
Mark
10/03/2021
Verified
Super slick, explained everything as we went through the process. Would highly recommend!
Paul
10/03/2021
Verified
I have been dealing with MitigateCyber for around 3 years now and in all that time they have always struck me as being very professional, very knowledgeable and always wanting to go that extra mile to help you in any way they can. I think the biggest recommendation I can give MitigateCyber is that I recommend them to colleagues within the industry.

Mark Carey
10/03/2021

